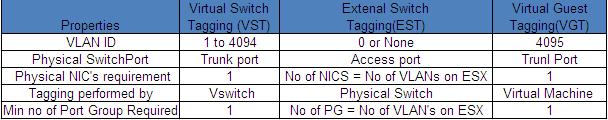
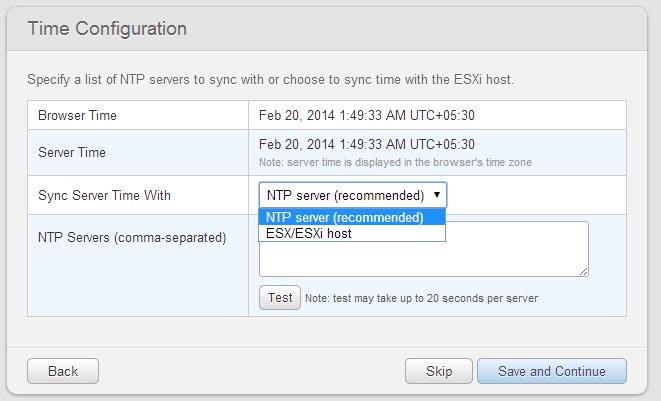
This post will be really helpful when you are troubleshooting your ESXi host network communication issue. As ESXi admin, We will not be knowing much information about the physical switch configuration for our ESXi host but still we will be able to get the phsyical switch information using the CDP (Cisco Discovery Protocol). The Cisco Discovery Protocol (CDP) is a Cisco’s proprietary Data Link Layer protocol used to share information about other directly connected Cisco equipment, such as upstream Physical switch.
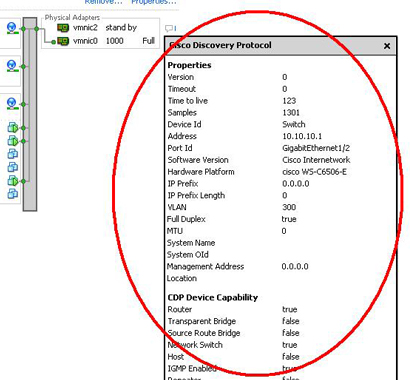
CDP allows ESX and ESXi administrators to determine the vSwitch is connected to which Cisco switch port. You will be able to see the properties of the Cisco switch, such as device ID, software version, and timeout from the vSphere Client when the CDP is enabled on the vSwitch. This information is useful when troubleshooting network connectivity issues related to VLAN tagging methods on virtual and physical port settings.
![CDP information]()
Image thanks for VMware.com
Good to know. Ok, Let’s imagine the situation, ESXi host is not reaching in the network. You are not able to connect to your ESXi host using Putty or vSphere Client. How to do identify the CDP information and collect the network switch and Port details in which your ESXi host vSwitch or vmnic is connected. This post helps you to achieve this just from the ESXi shell from your console Connection such as ILO or DRAC. This command can also be used when you connect your ESXi host using SSH connection.
Execute the below command to identify the Switch Name and Switch Port ID in which your vmnic “vmnic0″ is Connected:
~ # vim-cmd hostsvc/net/query_networkhint –pnic=vmnic0 | egrep ‘portId|devId’
devId = “cisco-swt1.vmwarearena.com(SSI55030KNE)”,
portId = “Ethernet107/1/13″,
In the baove command, DevID is the Switch name and PortId is the Ethernet port on the switch.
Execute the below command to identify the Switch Name and Switch Port in which you vmnic “vmnic1″ is Connected:
~ # vim-cmd hostsvc/net/query_networkhint –pnic=vmnic1 | egrep ‘portId|devId’
devId = “cisco-swt1.vmwarearena.com(SSI55030KNE)”,
portId = “Ethernet108/1/13″,:
Execute the below command to identify the VLAN Id’s which are tagged for your vmnic “vmnic1″:
~ # vim-cmd hostsvc/net/query_networkhint –pnic=vmnic1 | egrep ‘vlan’
vlanId = 32,
vlanId = 87,
vlanId = 88,
vlanId = 89,
vlanId = 3052,
vlanId = 0,
vlanId = 3061,
vlanId = 59,
vlan = 1,
VLAN’s which are visible from the command output are listed by your vmnic using CDP. There may be a chance that some vlan’s which are tagged by not visible in the above command. It is best to collaborate with your network team to get more detailed networking information.
Execute the below command to Get the observed IP subnet information of your vmnic “vmnic1″ :
~ # vim-cmd hostsvc/net/query_networkhint –pnic=vmnic1 |egrep ‘ipSubnet’
ipSubnet = “192.161.28.224-192.161.28.254″,
ipSubnet = “192.162.27.206-192.162.27.206″,
ipSubnet = “192.164.83.171-192.164.83.171″,
ipSubnet = “192.162.10.1-192.162.11.254″,
ipSubnet = “192.162.125.2-192.162.125.2″,
ipSubnet = “192.161.1.1-192.161.1.1″,
ipSubnet = “172.16.192.128-172.16.192.143″,
ipSubnet = “0.0.0.1-255.255.255.254″,
Execute the below command to collect the complete network hint information for your vmnic “vmnic1″. It displays the the VLAN info, IP address information, Physical Switch name, Physical Switch information like switch model, software version ,location,etc and network configurations of the physical switch.
~ # vim-cmd hostsvc/net/query_networkhint –pnic=vmnic1
(vim.host.PhysicalNic.NetworkHint) [
(vim.host.PhysicalNic.NetworkHint) {
dynamicType = <unset>,
device = "vmnic1",
subnet = (vim.host.PhysicalNic.NetworkHint.IpNetwork) [
(vim.host.PhysicalNic.NetworkHint.IpNetwork) {
dynamicType = <unset>,
vlanId = 32,
ipSubnet = "192.162.21.192-192.162.21.254",
},
(vim.host.PhysicalNic.NetworkHint.IpNetwork) {
dynamicType = <unset>,
vlanId = 87,
ipSubnet = "192.162.27.206-192.162.27.206",
},
(vim.host.PhysicalNic.NetworkHint.IpNetwork) {
dynamicType = <unset>,
vlanId = 88,
ipSubnet = "192.164.83.171-192.164.83.171",
},
(vim.host.PhysicalNic.NetworkHint.IpNetwork) {
dynamicType = <unset>,
vlanId = 89,
ipSubnet = "192.162.10.1-192.162.11.254",
},
(vim.host.PhysicalNic.NetworkHint.IpNetwork) {
dynamicType = <unset>,
vlanId = 3052,
ipSubnet = "192.162.125.2-192.162.125.2",
},
(vim.host.PhysicalNic.NetworkHint.IpNetwork) {
dynamicType = <unset>,
vlanId = 0,
ipSubnet = "192.161.1.1-192.161.1.1",
},
(vim.host.PhysicalNic.NetworkHint.IpNetwork) {
dynamicType = <unset>,
vlanId = 3061,
ipSubnet = "172.16.192.128-172.16.192.143",
},
(vim.host.PhysicalNic.NetworkHint.IpNetwork) {
dynamicType = <unset>,
vlanId = 59,
ipSubnet = "0.0.0.1-255.255.255.254",
}
],
connectedSwitchPort = (vim.host.PhysicalNic.CdpInfo) {
dynamicType = <unset>,
cdpVersion = 2,
timeout = 0,
ttl = 146,
samples = 11606,
devId = “cisco-swt1.vmwarearena.com(SSI55030KNE)”,
address = “192.162.160.24″,
portId = “Ethernet108/1/13″,
deviceCapability = (vim.host.PhysicalNic.CdpDeviceCapability) {
dynamicType = <unset>,
router = false,
transparentBridge = false,
sourceRouteBridge = false,
networkSwitch = true,
host = false,
igmpEnabled = true,
repeater = false,
},
softwareVersion = “Cisco Nexus Operating System (NX-OS) Software, Version 5.2(1)N1(4)”,
hardwarePlatform = ” N5K-C5596T “,
ipPrefix = “0.0.0.0″,
ipPrefixLen = 0,
vlan = 1,
fullDuplex = true,
mtu = 1500,
systemName = “cisco-swt1″,
systemOID = “1.7.6.1.5.1.9.12.13.1.3.1384″,
mgmtAddr = “192.162.160.24″,
location = “India,Bang-KR “,
},
lldpInfo = (vim.host.PhysicalNic.LldpInfo) null,
}
]
I hope this is informative for you. Thanks for Reading!!!. Be Social and share it in social media, if you feel worth sharing it.